- World Class Solutions
- 254 712 399544
- 254 722810084
- info@softlinkoptions.com
End to End Encryption

Data Masking
February 2, 2022
Flower Delivery Website
February 2, 2022What is End to End Encryption
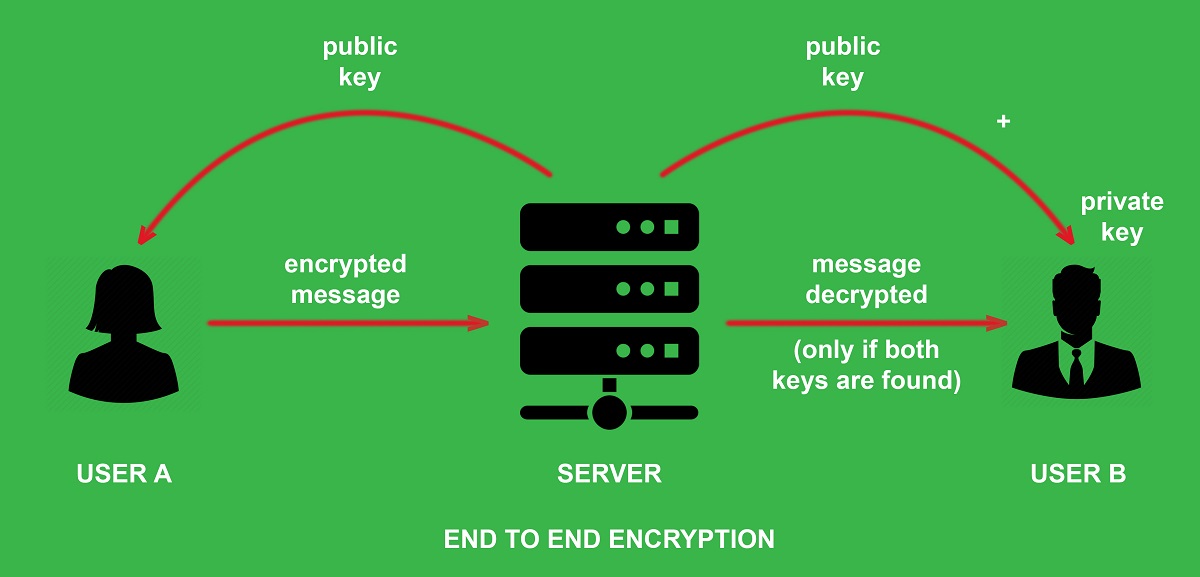
Email encryption is the encryption of email messages to protect the content from being read by entities other than the intended recipients. Email encryption may also include authentication. End-to-end encryption (E2EE) is a communication system where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers from accessing the cryptographic keys needed to decrypt the conversation. These eavesdroppers include telecom providers, internet providers, malicious state bodies, and even communication service providers. Some end-to-end encrypted communication services allow users to use their public key on every computer they log into. This provides transparent end-to-end encryption. However, other communication services require end-users to install browser extensions to use their cryptographic keys across multiple computers. A good example is those that use client-side JavaScript. End-to-end encryption is a way of “tricking” email into thinking you’re sending end encrypted emails without actually doing it. The result is that the sender’s end doesn’t send your password and username, only from the receiver’s end. This way, if anyone ever intercepted the message, they wouldn’t find out the user’s password or username. In addition, the end-user can also verify at any time that you are who you say you are without worrying about someone intercepting the message.Benefits
Privacy and Safeguard from spammers
E2EE has many benefits. First, it prevents spammers from collecting email addresses and hides the message’s content from prying eyes like telecom providers and internet providers.
End-to-end encryption is good for privacy, good for business, and good for government relations. It protects users against surveillance, internet snooping, and data breaches. It is important to note that end-to-end encrypted emails may not be completely secure. Malicious state bodies can still hack encryption keys. However, through practices like key rotation, it is one of the most effective ways to keep your communications safe from prying eyes.
The result is end-to-end encrypted emails virtually indistinguishable from regular end-to-end encrypted emails. Moreover, with E2EE, not even your email provider will be able to read the contents of your email messages.End to End Encryption and the Law
End-to-end encryption has become an issue because of recent changes in the law where emails are no longer private; prosecutors can subpoena for legal cases. This forces end-users to use end-to-end email encryption to keep their messages secure and away from prying eyes like governments or authorities. In many countries nowadays, such actions by the government are illegal. There is a growing worldwide trend of legislation curbing spying and eavesdropping by state authorities. In Kenya, there is an ongoing debate on data protection laws. This has resulted from recent changes in the Data Protection Act. The government seeks more power to infringe on people’s privacy. There are also less obvious benefits like preventing email providers from selling user data to advertisers. This has become a critical issue in the big data capitalistic world we live in. Organizations are investing in access to private data to achieve their marketing objectives.Problems
Technical limitations for end-users
First, E2EE systems may be difficult to adopt for the typical end-user. For example, end-users must typically manually manage their private keys to ensure that no other party can read their messages. This requires end-users to possess strong technical skills, and individuals must take great care to avoid losing private keys. This is not just a problem for end-users but can also create issues for organizations where end users communicate with each other. It prevents the organization from having an overview of which employees have access to private information.
In addition, it can be cumbersome when hackers hack encryption keys, or encrypted emails become inaccessible for several reasons. For example, the server may not send encrypted emails Due to bugs in end-to-end encryption implementations. This presents a significant challenge to end-users with limited technical skills.
Authentication and end to end encryption
The end-to-end encryption methods used by communication services, such as Signal (software), are designed to protect end users only. Therefore, these E2EE communication services do not provide end-users with the ability to authenticate or encrypt their connections with other end users of that service. This lack of authentication can be a significant security problem for end-users, as that may allow denial-of-service attacks on end-users.
E2EE technologies may promote security-related awareness and legislation to protect end-users from being unaware of the risks.
End to end encryption only protects the message, not the system.
End-to-end encryption typically does not protect the end systems involved. Only the content of messages as it passes over the wire. So, spammers can still collect email addresses, and malicious individuals can insert malware into endpoints. In addition, E2EE requires the authentication of the end-users. This makes an end to end email encryption very difficult in public key infrastructure (PKI) certificates. It applies when using older protocols such as PGP and S/MIME.
E2EE is a necessity today for all organizations. The benefits outweigh the drawbacks in this digital age. Data leakages and breaches have resulted in massive losses for organizations. Furthermore, it protects individuals from potential lawsuits and reputational damages.
At Softlink Options, we work with all organizations invested in big data that require data security solutions. Check out our data backup and web hosting packages. CONTACT US in case of any queries. We take pride in the quality of our products and services.